<aside>
💡
Quick Facts
- The Blend Network provides an additional layer of anonymity for block proposers on top of Cryptarchia's Private Proof of Stake consensus.
- It is optimised for scarce communication patterns with quotas on message frequency and path lengths, minimising bandwidth usage while maintaining strong anonymity guarantees.
- Proposals are encrypted in multiple layers and routed through random paths of nodes, with each node decrypting one layer and adding random delays before forwarding.
- The network generates indistinguishable cover messages that mimic real proposals, creating network noise that prevents observers from identifying genuine block proposals.
</aside>
On Logos, privacy for block proposers comes built-in with its Private Proof of Stake (PPoS) consensus protocol, Cryptarchia. It serves as a first line of defence against deanonymisation by using a private leadership election to protect block proposers. However, preventing adversaries from learning details about proposers by monitoring network activity requires even more robust obfuscation strategies.
Logos’ Blend Protocol was designed to be exactly that: an anonymous broadcasting protocol for scarce communication patterns that makes it harder to link a block proposal with its proposer based on network analysis. It does this by introducing cryptographic and timing obfuscation to the proposal process, making it difficult to distinguish proposals from each other. The Blend Network - the Bedrock Service consisting of nodes participating in the Blend Protocol - is therefore an integral part of the Logos Blockchain architecture.
Objectives
The main objective of the Logos Blend Network ****is to reduce the probability of linking a block proposal with its proposer, which also translates to increasing the difficulty of learning the proposer’s relative stake. At the same time, the Blend Protocol was designed to minimise bandwidth usage on the network compared to general-use mixnets, and to maximise decentralisation by involving all nodes in the obfuscation process. By doing so, the Blend Network increases the cost of attacking the network to deanonymise a block proposal without straining the network with high bandwidth usage.
The Blend Network supports the privacy of the Logos Blockchain as a whole, by providing additional anonymity to block proposers - protecting against adversaries with both a complete (global) and partial (local) view of the Logos Blockchain. The anonymity provided by the Blend Network also substantially improves the privacy guarantees of Cryptarchia by making it even harder to learn a proposer’s relative stake - which would allow an attacker to estimate the likelihood of that node winning the leadership election.
Blend Protocol Overview
The Blend Network makes it difficult to link a block proposer to their proposal by having the message travel between several nodes before being revealed. Blend nodes must maintain a minimum number of connections with other nodes, and cannot exceed a maximum frequency of messages they can send - putting an upper bound on bandwidth usage.
While dedicated participation in the Blend Network is reserved for declared Blend nodes, proposals can also be sent to it from regular Logos nodes. The following steps illustrate the process which a proposal message goes through before being broadcast and included in the chain.
-
The message sender selects a random path of nodes along which it will relay its message to the receiver, covering the message in layers of encryption for every node on the path.
-
The sender sends the layered message to every Blend node with which it maintains a peer-to-peer connection. This process, known as dissemination, is shown below.
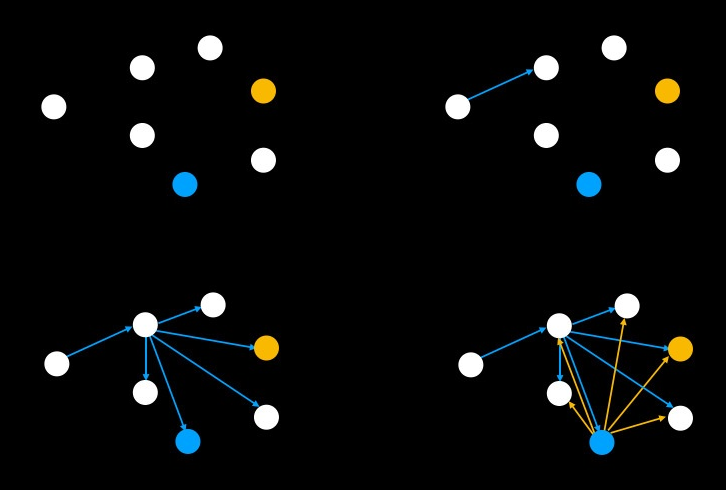
The Blend Network using dissemination to relay proposal messages. Peer-to-peer relaying of messages is not shown for simplicity.
-
When a Blend node receives a message, it checks that the message is unique and has not yet been seen, relaying it to its own peers. This ensures that every message is ultimately disseminated to the entire network.
-
A Blend node that receives a message will also attempt to decrypt the message. If it is able to decrypt the outer layer of a message it receives, it relays this decrypted message (after a randomised delay) to its peers for the next node in the path to receive and decrypt.
-
When the receiver finally receives its message, it decrypts this message and is able to retrieve the original payload. This payload is then broadcast to the Logos Blockchain as a block proposal.
This process of hiding messages under several layers of encryption and randomly delaying their propagation at each stage of dissemination is known as message blending. When a message is disseminated to all nodes, observers cannot determine which node was the intended receiver, even if they can identify the sender. Due to the layered encryption, observers also cannot determine which “hop” of the relay process the message is currently on. This decryption at each node in the path transforms messages, so the incoming and outgoing messages cannot be linked together based on their content.
Random delays are the other component of message blending. If messages are rare (as in a low bandwidth network like the Blend Network), then an observer may be able to link even encrypted messages if they are disseminated in close succession. To prevent this, every message is assigned a random delay by the node processing it, with each message being released in the order it is received once its delay period has passed. This ensures that incoming and outgoing messages cannot be linked together based on their timing.
Cover Traffic
An important way that the Blend Network obscures network patterns is by producing indistinguishable messages within a “crowded” network. To increase this effect in an environment where proposals are relatively rare, the Blend Network also produces artificial cover messages. Cover messages do not contain any meaningful payload and are generated by Blend nodes to increase network noise and to blend in with data messages that contain real proposals.
Cover messages mimic the behavior of data messages, in that they are disseminated and processed by Blend nodes in the same manner. Blend nodes repeatedly encrypt random payload data to generate a cover message, which is then relayed to the next node in its selected path via dissemination. At each step in the transmission process, intended nodes decrypt, randomly delay, and disseminate cover messages without any indication that they may not be genuine. In fact, encrypted data and cover messages are completely indistinguishable even to adversary-controlled Blend nodes (a type of local observer). The hiding effect provided by cover traffic is illustrated in the diagram below.
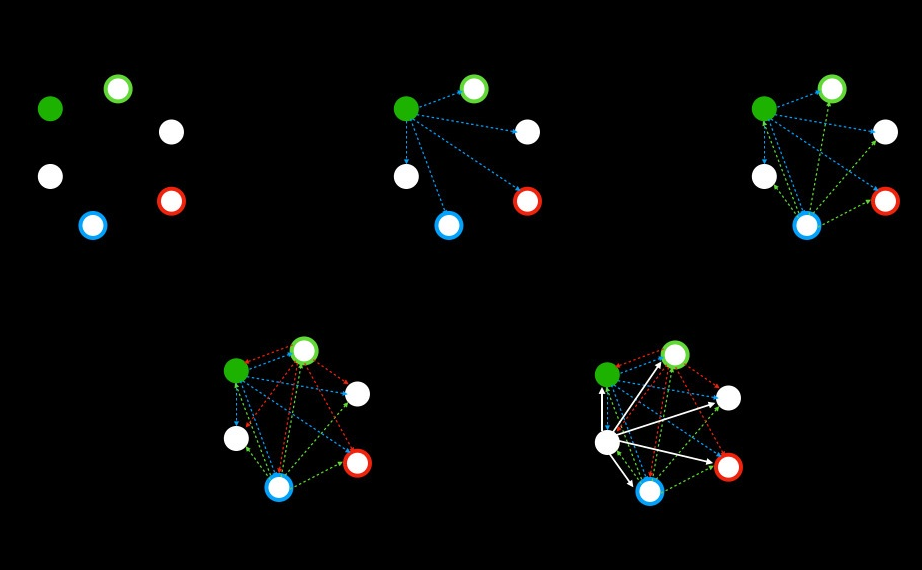
Disseminated Blend Network cover traffic (dotted lines) obscuring a data message (solid lines).

